EID (eUICC ID): The Digital Identity of eSIM Technology
In the world of eSIM technology, the EID (eUICC ID) serves as a fundamental digital identifier, playing a crucial role in the secure provisioning and management of eSIM profiles. While consumers rarely interact with this identifier directly, it forms the backbone of the eSIM ecosystem, enabling the secure, remote management of mobile connectivity.
This article explores the EID in depth, examining its structure, purpose, security implications, and role in the broader eSIM landscape.
What is an EID (eUICC ID)?
The EID, or eUICC Identifier, is a globally unique permanent identifier that is programmed into every eUICC chip during the manufacturing process. Similar to how every physical device has a unique serial number, every eUICC chip has a unique EID that distinguishes it from all other eUICC chips worldwide.
This identifier serves as the digital identity of the eUICC chip and, by extension, the device in which it is embedded. The EID is immutable—it cannot be changed or reprogrammed after the chip is manufactured, ensuring a permanent and reliable identifier throughout the device’s lifecycle.
Structure and Format of the EID
The EID follows a standardized format defined by the GSMA (Global System for Mobile Communications Association) in their specifications for Remote SIM Provisioning. The EID is a 32-digit hexadecimal number, typically represented in the following format:
“`89049032004001234567890123456789“`
This 32-digit identifier is structured according to specific rules:
1. First 2 digits (89): Represent the industry identifier for telecommunications, as defined by ISO/IEC 7812.
2. Next 10 digits (0490320040): Identify the eUICC manufacturer and provide information about the chip model and version.
3. Remaining 20 digits (01234567890123456789): Constitute a unique serial number assigned by the manufacturer to the specific eUICC chip.
The EID is often printed on the packaging of eSIM-enabled devices or can be accessed through the device’s settings menu, though many consumer devices hide this technical detail from end-users to simplify the interface.
The Role of EID in Remote SIM Provisioning
The EID plays a central role in the Remote SIM Provisioning (RSP) process, which is the foundation of eSIM technology. Here’s how the EID facilitates this process:
1. Device Identification
When a user wants to download a mobile operator profile to their eSIM-enabled device, the device must first be uniquely identified within the eSIM ecosystem. The EID serves as this unique identifier, allowing the provisioning system to recognize the specific eUICC chip that will receive the profile.
2. Subscription Association
The EID is used by the mobile operator’s Subscription Manager Data Preparation (SM-DP+) server to associate the device with a specific customer subscription. This association ensures that the correct profile is prepared and delivered to the intended device.
3. Secure Channel Establishment
Perhaps most importantly, the EID is used to establish a secure communication channel between the device and the provisioning server. This secure channel ensures that sensitive information, such as authentication keys and subscriber identities, can be transmitted safely without risk of interception or tampering.
4. Profile Management
Throughout the lifecycle of the device, the EID continues to serve as the reference identifier for all profile management operations, including downloading additional profiles, enabling or disabling profiles, and deleting profiles that are no longer needed.
EID in the eSIM Ecosystem Architecture
To understand the significance of the EID, it’s helpful to examine its place within the broader eSIM ecosystem architecture:
Consumer eSIM Architecture
In the consumer eSIM architecture, several key components interact with the EID:
1. LPA (Local Profile Assistant): This is the software on the device that manages eSIM profiles. The LPA uses the EID to identify the device to remote servers.
2. SM-DP+ (Subscription Manager – Data Preparation): This server, operated by or on behalf of mobile operators, prepares and securely delivers eSIM profiles. It uses the EID to encrypt profiles specifically for the target device.
3. SM-DS (Subscription Manager – Discovery Service): This optional global service helps devices locate the correct SM-DP+ when they need to download a profile. The EID is used as a lookup key in this discovery process.
When a consumer initiates the process of downloading an eSIM profile (typically by scanning a QR code), the following EID-related steps occur:
1. The QR code contains the address of the operator’s SM-DP+ server.
2. The device’s LPA connects to the SM-DP+ and provides the EID.
3. The SM-DP+ uses the EID to prepare a profile specifically encrypted for that device.
4. A secure channel is established using cryptographic keys derived in part from the EID.
5. The encrypted profile is downloaded to the device and installed on the eUICC.
 M2M (Machine-to-Machine) eSIM Architecture
M2M (Machine-to-Machine) eSIM Architecture
In the M2M architecture, which is designed for IoT and industrial applications, the process is slightly different, but the EID plays a similar role:
1. SM-SR (Subscription Manager – Secure Routing): This component, specific to the M2M architecture, manages the secure connection to eUICCs. It uses the EID to identify and authenticate the target eUICC.
2. SM-DP (Subscription Manager – Data Preparation): Similar to the consumer architecture, but with different protocols optimized for M2M applications.
In M2M scenarios, profile management is typically initiated by the operator rather than the end-user, but the EID still serves as the critical identifier that enables secure communication with the specific eUICC.
Security Implications of the EID
The EID plays a significant role in the security architecture of eSIM technology:
Cryptographic Foundation
The EID serves as part of the cryptographic foundation for secure communication. While the EID itself is not a secret (it can be read from the eUICC and is sometimes printed on device packaging), it is used in combination with other secret keys to establish secure channels.
Anti-Cloning Protection
The immutable nature of the EID helps prevent cloning attacks. Since each eUICC has a unique EID that cannot be changed, it becomes much more difficult to create counterfeit eUICCs that can successfully impersonate legitimate devices.
Privacy Considerations
While the EID is a permanent identifier, eSIM implementations include measures to protect user privacy. The EID is primarily used in the background during profile management operations and is not typically exposed during normal network operations, where temporary identifiers are used instead.
Secure Storage
The EID is stored in a secure area of the eUICC chip, protected by the same hardware security measures that protect other sensitive information like authentication keys. This secure storage helps prevent unauthorized access or tampering.
EID in Different Device Categories
The implementation and usage of the EID vary slightly across different device categories:
Smartphones
In smartphones, the EID is typically accessible through the settings menu, though it may be hidden in advanced or developer options to avoid confusing non-technical users. When setting up an eSIM, the smartphone’s operating system handles the EID automatically, so users rarely need to interact with it directly.
Wearables
For wearables like smartwatches, the EID is often managed through a companion smartphone app. The app handles the profile download process, using the wearable’s EID behind the scenes without requiring user intervention.
IoT Devices
In IoT applications, the EID takes on even greater importance as these devices often lack user interfaces. IoT device manufacturers typically record the EIDs of their devices during production and provide this information to mobile operators or IoT platform providers to enable remote provisioning.
Challenges and Considerations Related to EID
Despite its critical role, the EID presents several challenges in the eSIM ecosystem:
Limited User Visibility
Most consumers are unaware of the EID and its role, which can create challenges when troubleshooting connectivity issues. Technical support staff may need to guide users through finding their device’s EID when resolving certain problems.
EID Management for Enterprise
For enterprises deploying large numbers of eSIM-enabled devices, managing and tracking EIDs can become complex. Enterprise mobility management systems are evolving to incorporate EID tracking as part of their device management capabilities.
Regulatory Considerations
In some jurisdictions, permanent identifiers like the EID may be subject to privacy regulations. Device manufacturers and operators must ensure their handling of EIDs complies with relevant data protection laws.
EID Provisioning in Manufacturing
For device manufacturers, securely programming and recording EIDs during the manufacturing process requires careful management to ensure uniqueness and proper documentation.
Future Developments Related to EID
As eSIM technology continues to evolve, several developments related to EID are on the horizon:
Integration with Digital Identity
The EID could potentially play a role in broader digital identity ecosystems, serving as one component of a device’s verifiable identity for various online services.
Enhanced Privacy Protections
Future specifications may introduce additional privacy-enhancing technologies to further minimize exposure of the permanent EID during normal operations.
iSIM Evolution
As the industry moves toward integrated SIM (iSIM) technology, where SIM functionality is integrated directly into the device’s main processor, the concept of the EID will likely evolve while maintaining its core purpose as a unique identifier.
Standardization Across Industries
As eSIM adoption expands beyond traditional mobile devices into new sectors like automotive, healthcare, and industrial applications, we may see additional standardization of EID usage patterns specific to these industries.
Practical Implications for Users
While the EID operates largely behind the scenes, there are a few practical implications for end-users:
Finding Your Device’s EID
If you need to find your device’s EID (which might be necessary when working with technical support), the method varies by device:
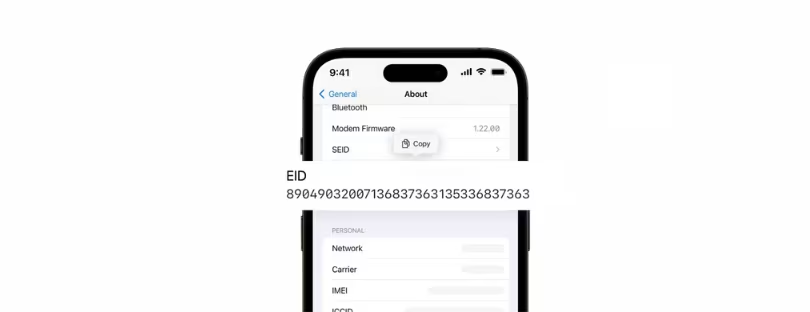
– On iPhone: Go to Settings > General > About > EID
– On Android: The location varies by manufacturer, but typically can be found in Settings > About phone > SIM status or Settings > Connections > SIM manager > eSIM info
– On Windows devices: Settings > Network & Internet > Mobile > eSIM > Advanced Options
EID and Device Replacement
When replacing an eSIM-enabled device, you cannot transfer the EID to the new device (as it is permanently assigned to the eUICC chip). Instead, you’ll need to download new profiles to the new device, which will have its own unique EID.
EID and Privacy
From a privacy perspective, users should treat the EID similar to other device identifiers like IMEI numbers—it’s generally safe to share with legitimate mobile operators and authorized service providers, but should not be publicly disclosed unnecessarily.
Conclusion
The EID (eUICC ID) is a fundamental component of eSIM technology that enables the secure, remote management of mobile connectivity profiles. As a permanent, unique identifier programmed into every eUICC chip during manufacturing, the EID serves as the digital identity that allows provisioning systems to target specific devices, establish secure communication channels, and manage profiles throughout the device lifecycle.
While most consumers will never need to directly interact with their device’s EID, understanding its role provides valuable insight into how eSIM technology works behind the scenes. As eSIM adoption continues to grow and evolve, the EID will remain a critical element in the secure, flexible connectivity that eSIM technology enables.
The next time you effortlessly download a mobile plan to your smartphone or activate a new smartwatch without inserting a physical SIM card, remember that the invisible EID is working behind the scenes, ensuring that this convenient process remains secure and reliable.






 M2M (Machine-to-Machine) eSIM Architecture
M2M (Machine-to-Machine) eSIM Architecture





